Send
Close Add comments:
(status displays here)
Got it! This site "www.robinsnyder.com" uses cookies. You consent to this by clicking on "Got it!" or by continuing to use this website. Note: This appears on each machine/browser from which this site is accessed.
The XOR operation and one-time pads
1. The XOR operation and one-time pads
A
OTP (One Time Pad) cipher system that uses the cipher key one time only, and for short messages (key is longer than the message).
The most secure keys are one-time pads of random, but agreed-on keys. It is impossible to break a one-time pad. But, if the key is ever reused, then it becomes almost trivial to break that one-time pad.
That is why it is called a one-time pad. It can only (securely) be used one time.
The one-time pad was first described in 1882 and re-discovered in 1917 by Gilbert Vernam.
2. History
This is the only known secure system (unbreakable if properly used) for communication, but it has some restrictions that must be insured.
The problem with the one time pad is that of key distribution. Other message security systems are typically based on this system at an internal level, but use a more convenient way to generate a pseudo-random sequence of bits.
3. Brute force attack
Given a sequence of random bits, the problem reduces to guessing that sequence of random bits.
This is not possible, since a brute force attack is not possible (for more than a line of text) and such an attack would generate every possible random message and every possible meaningful message.
4. Exclusive or
The
XOR (Exclusive Or) operation is true if both operands are different. Here is the extended truth table of the XOR operation using the caret "
^N" is the exclusive or operator.
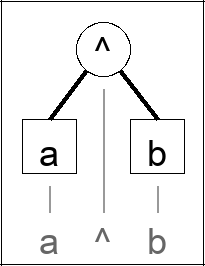
a b | a b
-----------
0 0 | 0 0 0
0 1 | 0 1 1
1 0 | 1 1 0
1 1 | 1 0 1
5. One-time pad proof
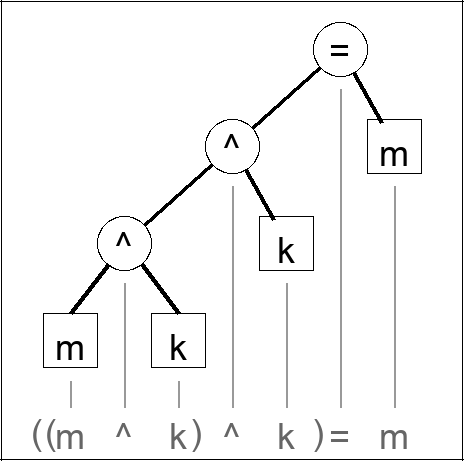 m is the message
k is the key
m is the message
k is the key
The proof is for one random bit and one bit of the message. Repeat for a longer message (always using a new random bit).
k m | ( ( m k ) k ) = m
---------------------------
0 0 | ( ( 0 0 0 ) 0 0 ) 1 0
0 1 | ( ( 1 1 0 ) 1 0 ) 1 1
1 0 | ( ( 0 1 1 ) 0 1 ) 1 0
1 1 | ( ( 1 0 1 ) 1 1 ) 1 1
The extended truth table shows that encrypting by a random bit and then applying the same operation results in the original value.
6. Re-order and re-name the variables
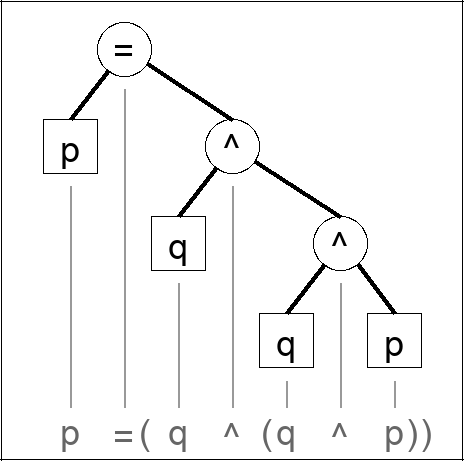 p is the message
q is the key
p is the message
q is the key
The proof is for one random bit and one bit of the message. Repeat for a longer message (always using a new random bit).
p q | p = ( q ( q p ) )
---------------------------
0 0 | 0 1 ( 0 0 ( 0 0 0 ) )
0 1 | 0 1 ( 1 0 ( 1 1 0 ) )
1 0 | 1 1 ( 0 1 ( 0 1 1 ) )
1 1 | 1 1 ( 1 1 ( 1 0 1 ) )
7. Key
01011001110111000000
10000011110100011110
11111000101111100010
00100100111100100110
10111000011110010011
01011000110111001001
10011110001011001110
00100010110110110110
10111010010100011111
00001100100011100010
Here is a (pseudo-random key). In actual use, a truly random key should be used.
8. Message#1
00000000000000000000
01111111111111111110
01000000000000000010
01000000000000000010
01000000000000000010
01000000000000000010
01000000000000000010
01000000000000000010
01111111111111111110
00000000000000000000
Here is message#1. The message is a rectangle within the bit pattern.
9. Encode#1
01011001110111000000
11111100001011100000
10111000101111100000
01100100111100100100
11111000011110010001
00011000110111001011
11011110001011001100
01100010110110110100
11000101101011100001
00001100100011100010
Here is encoded message#1. Message#1 has been fully encrypted using the key.
10. Decode#1
00000000000000000000
01111111111111111110
01000000000000000010
01000000000000000010
01000000000000000010
01000000000000000010
01000000000000000010
01000000000000000010
01111111111111111110
00000000000000000000
Here is decoded message#1. Message#1 has been completely recovered.
11. Message#2
01100000000000000110
00011000000000011000
00000110000001100000
00000001100110000000
00000000011000000000
00000001100110000000
00000110000001100000
00011000000000011000
01100000000000000110
10000000000000000001
Here is message#2. The message is a diagonal slash from each opposing corner.
12. Encode#2
00111001110111000110
10011011110100000110
11111110101110000010
00100101011010100110
10111000000110010011
01011001010001001001
10011000001010101110
00111010110110101110
11011010010100011001
10001100100011100011
Here is encoded message#2. Message#2 has been fully encrypted using the key.
13. Decode#2
01100000000000000110
00011000000000011000
00000110000001100000
00000001100110000000
00000000011000000000
00000001100110000000
00000110000001100000
00011000000000011000
01100000000000000110
10000000000000000001
Here is decoded message#2. Message#2 has been completely recovered.
14. Mixture
01100000000000000110
01100111111111100110
01000110000001100010
01000001100110000010
01000000011000000010
01000001100110000010
01000110000001100010
01011000000000011010
00011111111111111000
10000000000000000001
Here is XOR of encoded message#1 and encoded message#2. Re-using the key results in parts of each message being clearly visible. Once a lot of the message is broken, the rest is much easier to break.
15. Observation
Can you see parts of message#1 and message#2 in the mixture?
This results from using (or re-using) the same key.
In practice, it may not be as easy as this because of aligning a re-used key with a message, but the breaking of the code is much easier than the impossible breaking of the original code (if using a truly random key).
16. End of page


